TCP #93: We cut audit time by 40% with three changes
Documentation-as-system beats documentation-as-project.
You can also read my newsletters from the Substack mobile app and be notified when a new issue is available.
Audits don’t expose technical failures.
They expose the gap between what you claim and what you can prove.
The Audit Finding
Three weeks into the audit, we received one question from the auditor:
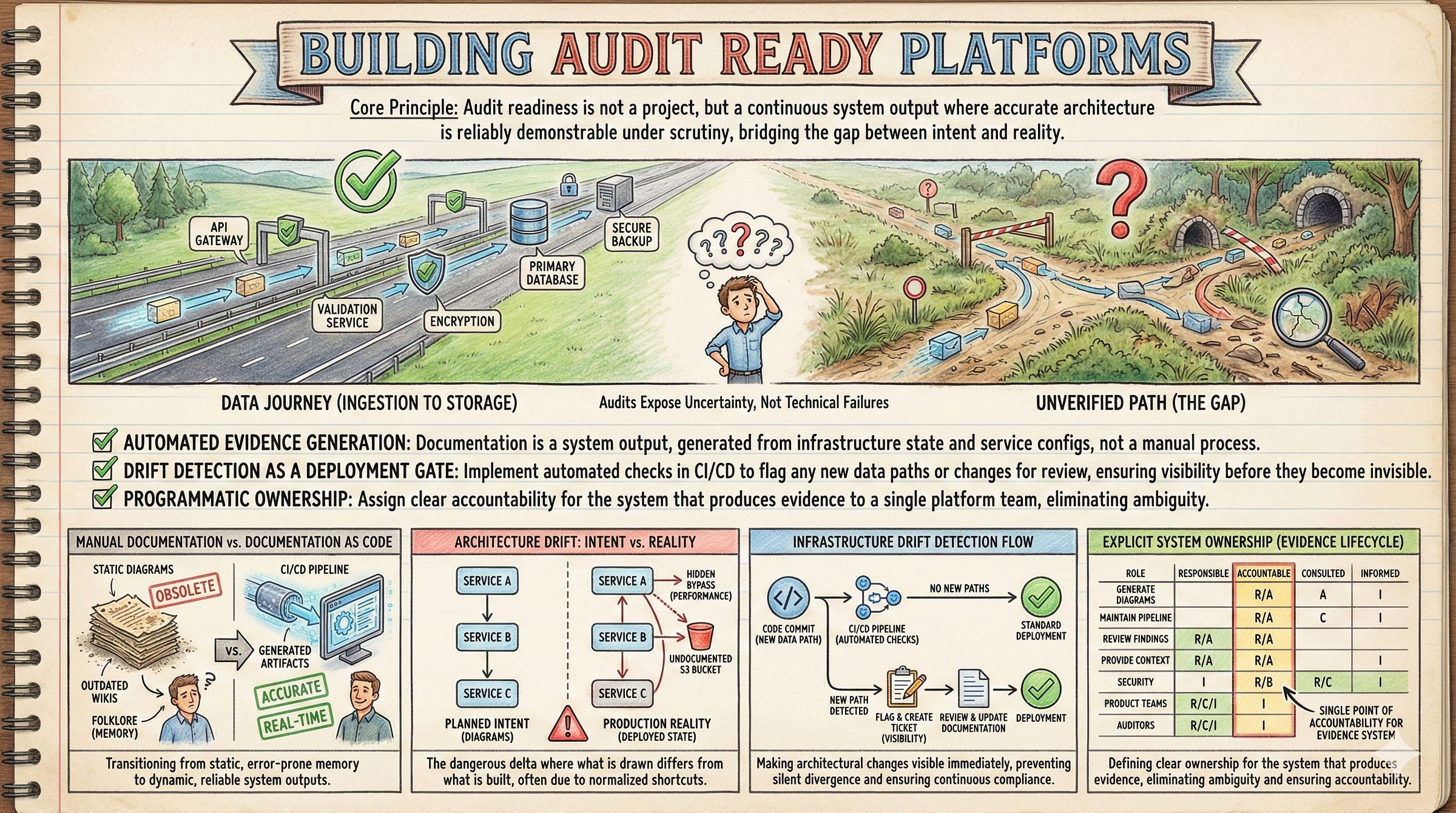
“Show me the path this customer record takes from ingestion to storage.”
We couldn’t answer it. Not precisely. Not in a way that matched our diagrams.
The architecture we’d drawn wasn’t the architecture we’d built.
What the Auditor Saw
Evidence packages submitted on schedule. Policies documented. Access reviews current.
On paper, everything was fine.
The auditor wanted to trace a single record from the API gateway through the database to the backup and verify that it matched our data flow diagrams.
What she saw: hesitation. Engineers opening multiple consoles. Sidebar conversations. “I think it goes through this service, but let me check.”
Leadership saw a team handling questions.
The auditor saw a team that couldn’t answer a basic question about their own system without checking three sources.
The symptom wasn’t a failed control.
It was uncertainty.
In regulated environments, uncertainty is the finding. It signals the organization doesn’t control what it claims to control.
The Architecture Drift We’d Normalized
We had architecture diagrams for different audiences.
One for security reviews. One for onboarding. One for the board.
None were wrong. None were complete.
The API gateway in our diagrams existed. But three services bypassed it, added over the past year for “performance reasons.” In production. Handling customer data. Not in any diagram.
No one made a bad decision. Each bypass was justified. Performance mattered. Deadlines mattered. The diagram update could wait.
It could always wait.
CloudFormation showed what we’d provisioned. Diagrams showed what we’d intended. Reality was the delta between them.
That delta stayed invisible until someone asked the right question.
We’d normalized drift because nothing had broken yet. The platform worked. Uptime was solid.
But “working” and “auditable” are different standards.
Why Documentation Drift Happens
Platform teams in regulated environments share a failure mode: the gap between “deployed” and “documented” grows silently.
No one notices until an external party forces reconciliation.
Engineers optimize for shipping.
Documentation trails behind.
Architecture diagrams live in tools disconnected from the infrastructure state.
Leadership measures uptime and deploy frequency, not documentation accuracy.
Auditors measure something else. Not whether your platform works. Whether you can prove it works the way you claim.
This asymmetry is dangerous.
Internal teams operate effectively because they have context. They know the workarounds. The exceptions. The “that diagram is outdated, but here’s how it actually works” conversations.
External parties don’t. Auditors. New hires. Incident responders at 3 am. They have only what’s written down.
Our real architecture wasn’t in Confluence. It was distributed across CloudFormation templates, CloudWatch logs, service meshes, and three engineers who’d been there since the beginning.
When one went on vacation during audit week, we lost critical context that existed nowhere else.
That’s not a documentation problem. That’s a single point of failure disguised as institutional knowledge.
The hard part isn’t creating documentation. It’s keeping it accurate as the system evolves.
The organizational root cause: we treated documentation as communication rather than control.
We updated the diagrams to explain concepts to users. Not as part of deployment. Not as a gate. Not as a system output.
Ownership was unclear. Infrastructure owned by CloudFormation. Security-owned policies. Product teams owned services. The space between the actual data flow and everyone else belonged to everyone.
Which meant no one.
No owner. No process. No accountability. Just drift.
How We Built Automated Architecture Documentation
Three changes. Not a documentation initiative. A system change.
Architecture diagrams became generated artifacts rather than authored documents.
We built a pipeline that produces data flow diagrams from infrastructure state and service configs. Documentation as code, not documentation as afterthought.
The diagrams weren’t prettier. They were accurate. Derived from reality, not memory.
When infrastructure changes, diagrams update automatically. No manual step. No “I’ll update that later.” No drift.
Infrastructure drift detection in CI/CD.
Any deployment that introduces a new data path automatically creates a ticket. Deployments aren’t blocked. Visibility is created.
The goal wasn’t to slow teams down. The goal was to make architectural changes visible before they became invisible.
Engineers still ship fast. Changes that affect data flow get flagged, reviewed, documented—by the system, not by humans remembering to do it.
Explicit ownership assigned to the platform team.
Not ownership of every diagram. Ownership of the system that produces them.
When the auditor asked, “Who owns this?” the answer was clear. One team. One Slack channel. One escalation path.
No more “I think infrastructure handles that” conversations. No ambiguity.
The finding was remediated in six weeks.
The real win came later. Next year’s audit took 40% less time. Auditors trusted the documentation. Less verifying. More sampling. The relationship shifted from adversarial to efficient.
That’s the ROI of automated compliance documentation. Not just passing audits. Passing them faster. With less stress. Fewer fire drills.
Audit Readiness as a System, Not a Project
Your architecture isn’t what you’ve deployed.
It’s what you can demonstrate under scrutiny.
Platform teams that pass audits cleanly aren’t the ones with the best technology. They’re the ones where documentation is a system output, not a manual process.
This is what separates teams that dread audits from teams that breeze through them.
This matters beyond compliance. Incident response depends on accurate architecture docs. Onboarding depends on them. Capacity planning. Security reviews. M&A due diligence.
Every function that needs to understand your system relies on documentation that reflects reality.
If that documentation is manually maintained, it’s already out of date. The moment you finish updating a diagram, the system has moved on. Manual processes can’t keep pace with continuous deployment.
Generated documentation can.
The question isn’t whether you have documentation.
The question is whether it would survive an auditor asking, “Prove it.”
If you can’t regenerate your architecture diagrams from infrastructure state, you don’t have documentation.
You have folklore.
Folklore doesn’t pass audits.
Speed is easy. Predictability is hard. I build platforms that deliver both.
Whenever you’re ready, there are 2 ways I can help you:
Free guides and helpful resources: https://thecloudplaybook.gumroad.com/
Get certified as an AWS AI Practitioner in 2026. Sign up today to elevate your cloud skills. (link)
That’s it for today!
Did you enjoy this newsletter issue?
Share with your friends, colleagues, and your favorite social media platform.
Until next week — Amrut
Get in touch
You can find me on LinkedIn or X.
If you would like to request a topic to read, please feel free to contact me directly via LinkedIn or X.