TCP #85: How AI Anomaly Detection Catches Security Breaches Traditional Tools Miss?
A comprehensive guide to implementing AI-powered security monitoring that stops attacks before they cause damage
You can also read my newsletters from the Substack mobile app and be notified when a new issue is available.
When I analyzed over 00 security incidents across enterprise environments, one pattern emerged that changed how I think about cybersecurity:
89% of successful breaches showed detectable anomalous patterns 2-4 hours before any damage occurred.
Yet in most cases, traditional security tools remained silent until it was too late.
Real examples that should have triggered alerts:
Marketing manager downloading 50GB of financial data at 2 AM
Service account accessing systems across three different geographic regions within minutes
Database queries that looked normal individually but revealed clear data harvesting patterns collectively
These weren't sophisticated zero-day exploits. They were behavioral anomalies that should have triggered an immediate investigation.
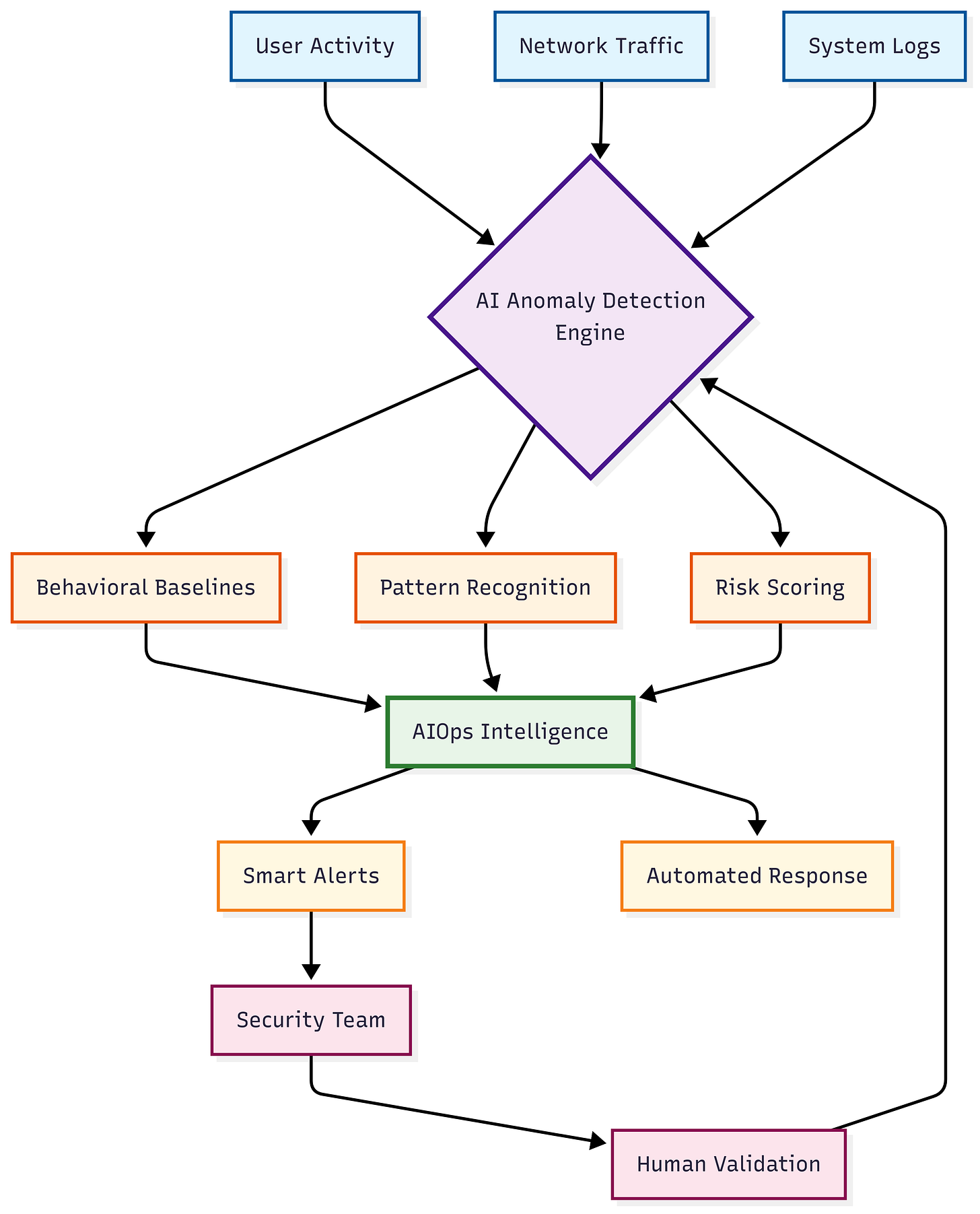
The AI Advantage: Learning Normal to Catch Abnormal
AI anomaly detection fundamentally shifts the security paradigm from "blacklist the bad" to "understand the normal."
Key Advantages:
Behavioral Baselines Over Static Rules
Dynamic baselines that adapt to legitimate business changes
Continuous learning from your specific environment
Context-aware risk assessment
Context-Aware Analysis
Considers user roles, time patterns, and system relationships
Evaluates events within a broader attack context
Reduces false positives through intelligent correlation
Proactive Threat Hunting
Identifies attack precursors before damage occurs
Catches early-stage compromise indicators
Provides a crucial early warning window
Building Effective Behavioral Baselines
The foundation of successful AI anomaly detection lies in establishing comprehensive behavioral baselines.
User Behavior Patterns
Access Patterns to Monitor:
Login times and geographic consistency
System access sequences and device fingerprints
Authentication method variations
Data Interaction Volumes:
Establish per-user baselines for data access
Monitor download volumes and file-sharing behaviors
Example: A User typically accessing 50 records/day suddenly pulls 5,000 records
Privilege Usage:
Administrative account behavior monitoring
Privilege escalation attempt detection
Cross-system access pattern analysis
Network Traffic Analysis
Connection Patterns:
Map typical network flows between systems
Monitor protocol usage and port combinations
Track data volume patterns
Geographic Consistency:
Flag connections from new geographic regions
Correlate with travel patterns and business operations
Red Flag: User connecting from three countries within one hour
Temporal Patterns:
After-hours activity monitoring
Weekend access from specific accounts
Unusual connection timing analysis
System Resource Utilization
Infrastructure Behavior Monitoring:
CPU, memory, and storage utilization baselines
Application performance metrics tracking
Warning Signs: Sudden CPU spikes indicating crypto mining or data processing
Practical Implementation: AWS Cloud-Native Solution
Start with existing cloud security services for immediate value:
☁️ AWS GuardDuty Implementation
Quick Setup:
aws guardduty create-detector --enable --finding-publishing-frequency FIFTEEN_MINUTES
Automatic Analysis of:
VPC Flow Logs for network anomalies
DNS queries for malicious domain detection
CloudTrail events for suspicious API activity
Pro Tip: Configure custom threat intelligence feeds for industry-specific threats
🕵️ Advanced User Behavior Analytics (UEBA)
User Entity Behavior Analytics represents one of the most effective AI security applications.
Identity-Centric Monitoring
Privilege Escalation Detection:
Monitor unusual permission requests
Track temporary privilege assignments
Red Flag: HR manager creating service accounts or modifying security groups
Access Time Deviations:
Individual user baseline establishment
Session duration and activity pattern monitoring
Example: Executive assistant accessing financial systems at midnight
Application Usage Changes:
Track user interactions across different applications
Warning Sign: Marketing user accessing database administration tools
Cross-Platform Correlation
Identity Federation Analysis:
Monitor authentication across different systems
Identify inconsistencies in authentication patterns
Multi-Cloud Activity Correlation:
Correlate user activities across cloud providers
Identify suspicious cross-platform access patterns
🤖 Machine Learning Models for Security
Understanding the technical approaches helps inform implementation decisions:
Unsupervised Learning Approaches
Isolation Forest:
Effective for high-dimensional security data outliers
Identifies anomalous behavior through partition analysis
Autoencoders:
Neural networks trained on normal behavior patterns
High reconstruction error indicates anomalous activity
LSTM Networks:
Long Short-Term Memory networks for sequential anomalies
Ideal for time-series security data analysis
Supervised Learning Applications
Random Forest Classifiers:
Categorize security events based on historical data
Effective for response prioritization
Gradient Boosting Models:
Excel at binary classification tasks
Distinguish legitimate vs. suspicious activities
🎯 Reducing Alert Fatigue Through Intelligence
AI's most valuable contribution: dramatically reducing false favorable rates
Risk-Based Scoring
Multi-Factor Risk Assessment:
User Context: Role-based risk weighting
Asset Criticality: Prioritize alerts for critical systems
Attack Chain Correlation: Identify coordinated campaigns
Behavioral Clustering
Peer Group Analysis:
Compare users against similar roles (not organization-wide averages)
Reduces false positives from legitimate role variations
System Grouping:
Cluster by function, criticality, and usage patterns
Establish more accurate behavioral baselines
🎣 Advanced Threat Hunting with AI
Beyond reactive monitoring: proactive threat identification
Domain Generation Algorithm (DGA) Detection
Many advanced malware families use algorithmic domain generation:
def detect_dga(domain):
entropy = calculate_entropy(domain)
consonant_ratio = count_consonants(domain) / len(domain)
return entropy > 4.5 and consonant_ratio > 0.7
AI Advantage: High-accuracy pattern identification for proactive C&C blocking
Lateral Movement Analysis
Network Graph Analysis:
Model normal communication patterns
Identify unusual paths suggesting reconnaissance
Credential Usage Patterns:
Track credential usage across systems
Identify credential stuffing or pass-the-hash attacks
☁️ Cloud-Specific Implementation
Modern cloud environments require specialized monitoring approaches:
Container and Kubernetes Security
Runtime Behavior Monitoring:
Analyze container behavior patterns
Identify deviations from intended application behavior
Resource Consumption Anomalies:
Monitor CPU, memory, and network usage within containers
Red Flags: Crypto mining, data exfiltration activities
Serverless Function Monitoring
Execution Pattern Analysis:
Establish baselines for function invocation patterns
Monitor execution duration and resource consumption
API Gateway Anomalies:
Monitor API call patterns and parameter variations
Identify reconnaissance or data harvesting attempts
Multi-Cloud Visibility
Cross-Platform Correlation:
Correlate activities across different cloud providers
Identify sophisticated multi-environment campaigns
Identity Federation Security:
Monitor federated identity usage patterns
Detect potential cross-platform privilege abuse
⚠️ Common Implementation Pitfalls
Training on Compromised Data
The Problem: Teaching AI systems that malicious behavior is normal
✅ The Solution:
Establish clean baseline periods through security assessments
Validate training data integrity with external security firms
Over-Reliance on Vendor Defaults
The Problem: Generic models don't align with organizational context
✅ The Solution:
Customize detection parameters for your environment
Configure threat intelligence feeds for your industry
Adjust alert prioritization for your risk profile
Poor Integration with Existing Processes
The Problem: AI alerts create operational friction
✅ The Solution:
Design implementations with existing workflows in mind
Ensure seamless SOAR platform integration
Align with analyst tools and ticketing systems
🔮 The Future of AI-Powered Security
As attack sophistication evolves, AI anomaly detection becomes increasingly critical for effective security postures.
Key Success Factor: Don't replace human expertise, augment it with AI capabilities that process vast amounts of data, identify subtle patterns, and provide early warning signals.
The organizations implementing these capabilities today gain significant advantages in detecting and responding to advanced threats.
🎯 Take Action Today
The threat landscape won't wait for perfect implementations.
Start Here:
Deploy cloud-native security services for immediate value
Establish comprehensive behavioral baselines across your environment
Gradually expand AI capabilities across your security stack
That’s it for today!
Did you enjoy this newsletter issue?
Share with your friends, colleagues, and your favorite social media platform.
Until next week — Amrut
Get in touch
You can find me on LinkedIn or X.
If you would like to request a topic to read, please feel free to contact me directly via LinkedIn or X.