TCP #98: AWS Multi-Account vs. Single-Account Strategy
Here is the framework I use to evaluate single-account vs. multi-account.
You can also read my newsletters from the Substack mobile app and be notified when a new issue is available.
Every growing platform team hits this fork in their AWS account strategy.
You have multiple workloads, multiple teams, and compliance requirements stacking up. Do you run everything in a single AWS account with tight IAM boundaries, or split into a multi-account structure with AWS Organizations?
I have managed 9 AWS accounts across 11 services for 9 tenants in regulated environments, including FedRAMP, ISO, and HIPAA.
The choice between single-account and multi-account AWS shapes your security posture, operational overhead, and audit readiness for years to come.
Get it wrong, and you are either retrofitting account isolation under audit pressure or drowning in cross-account complexity you did not need.
This is my decision framework for evaluating it.
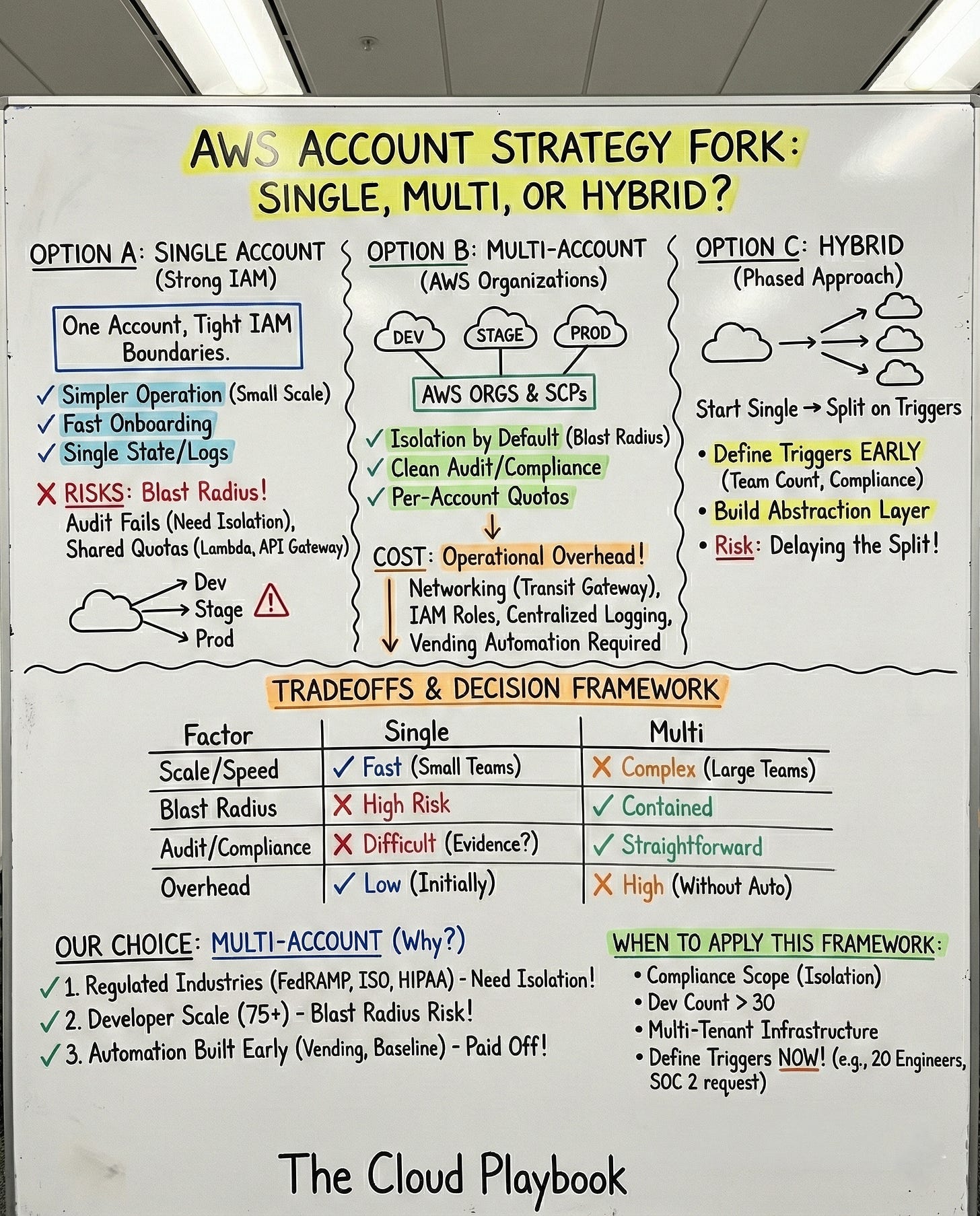
The Options (Single Account, Multi-Account, or Hybrid)
Option A: Single account with strong IAM boundaries.
You keep all workloads in one AWS account. You use IAM policies, resource tags, and service control boundaries to isolate teams and environments.
Billing stays centralized. Networking stays flat. You manage one set of CloudTrail logs, one GuardDuty configuration, and one Security Hub deployment.
Your Terraform state files share a single S3 backend. Everything lives under one roof, and your team operates with minimal AWS organizational overhead.
Option B: Multi-account with AWS Organizations.
You create dedicated accounts for each environment (dev, staging, prod), for each team, or for each tenant. You use AWS Organizations with SCPs for guardrails.
Each account gets its own blast radius boundary. Billing is segmented by default. You need a landing zone, centralized logging accounts, and cross-account role assumptions.
Option C: Hybrid, phased approach.
You start with a single account and split as triggers emerge. You define specific conditions, team count thresholds, compliance scope changes, blast radius incidents that force the migration.
You build the abstraction layer early, so the move is not a rewrite. Your Terraform modules reference account IDs as variables. Your CI/CD pipelines use role assumptions that work the same way whether the target is a local or remote account.
The Tradeoffs of Each AWS Account Strategy
A single account is simpler to operate at a small scale.
One set of IAM policies. One networking layer. One billing dashboard. Your platform team spends less time on account vending and cross-account permissions.
Onboarding a new engineer takes minutes, not hours. Your CI/CD pipelines do not need cross-account role assumptions. Your Terraform state lives in one place.
The cost shows up later.
When an S3 bucket policy misconfiguration in development exposes production data, you realize the blast radius was never contained.
When your auditor asks for evidence of environmental isolation, IAM policies alone do not satisfy the control. The auditor wants to ensure that a compromised set of dev credentials cannot access production resources, and that tag-based policies are not sufficient proof for most assessors.
When two teams hit the same service quota, and one of them is production, you scramble. I have seen Lambda concurrency limits, API Gateway throttling, and DynamoDB throughput all become shared bottlenecks across environments within a single account.
Multi-account gives you AWS account isolation by default.
A compromised dev account does not touch production. Service quotas are per-account, so a runaway Lambda in staging does not throttle your production workloads.
Cost attribution is automatic. Each account maps cleanly to a cost center or tenant. Auditors see clean environment separation, and your evidence collection for compliance becomes straightforward.
The cost is operational complexity.
Cross-account networking requires Transit Gateway or VPC peering, each with their own routing tables and security groups to manage. Centralized logging needs a dedicated account with S3 replication and cross-account CloudWatch access.
IAM roles must be assumed across accounts, adding latency and failure points to your CI/CD pipelines. Every new account needs a baseline: CloudTrail, Config, GuardDuty, Security Hub, and proper SCPs.
Without automation, provisioning and maintaining this baseline becomes a full-time job for your platform team.
The hybrid path sounds smart but carries its own risk.
If you do not define the migration triggers upfront, you will always find a reason to delay. And the longer you wait, the more tightly coupled your single-account architecture becomes, which makes the eventual split harder.
What We Chose and Why
We went multi-account from the start. Three factors drove the decision.
First, we operated in regulated industries.
FedRAMP, ISO, HIPAA. Each framework requires environment separation beyond IAM policies.
Auditors want to see account-level isolation between production and non-production. They want separate CloudTrail trails in separate accounts with restricted access.
They want to verify that a developer with access to a staging account cannot escalate to production resources through any path, not through IAM, not through networking, not through shared credentials.
Starting with an AWS multi-account strategy meant we never had to retrofit this evidence.
Second, we supported 75+ developers across the US, India, and Colombia.
At that team size, the blast radius risk of a single account was too high. One misconfigured AWS CDK module in development should not affect production.
Account boundaries enforce this without relying on everyone getting their IAM policies right. The boundary is structural, not behavioral. That matters at scale.
Third, we built the account vending automation early.
Account provisioning through AWS CDK modules. Baseline security controls applied through AWS Organizations SCPs. Centralized logging with cross-account replication on day one.
The upfront investment was significant, roughly three weeks of dedicated platform engineering time. The payoff was that every new account was production-ready in under an hour, with a full compliance baseline applied automatically.
When This AWS Multi-Account Framework Applies
Use this decision framework when you see any of these conditions:
Your compliance scope includes frameworks that require environment isolation. Your developer count is above 30. Your production workloads serve external customers. You run a multi-tenant infrastructure where tenant data must be segregated.
If you are a 5-person startup with one product and no compliance requirements, stay on a single account. Do not over-engineer.
But define the triggers now. Write them down.
“When our team hits 20 engineers.”
“When our first enterprise customer asks for a SOC 2 report.”
“When our first outage traces back to a dev environment change hitting production.”
These are not hypothetical. They are inevitable at scale.
The decision is not which AWS account strategy is better in the abstract. Which strategy matches your current constraints and the trajectory you are building toward?
Evaluate accordingly.
Whenever you’re ready, there are 2 ways I can help you:
Free guides and helpful resources: https://thecloudplaybook.gumroad.com/
Get certified as an AWS AI Practitioner in 2026. Sign up today to elevate your cloud skills. (link)
That’s it for today!
Did you enjoy this newsletter issue?
Share with your friends, colleagues, and your favorite social media platform.
Until next week — Amrut
Get in touch
You can find me on LinkedIn or X.
If you would like to request a topic to read, please feel free to contact me directly via LinkedIn or X.