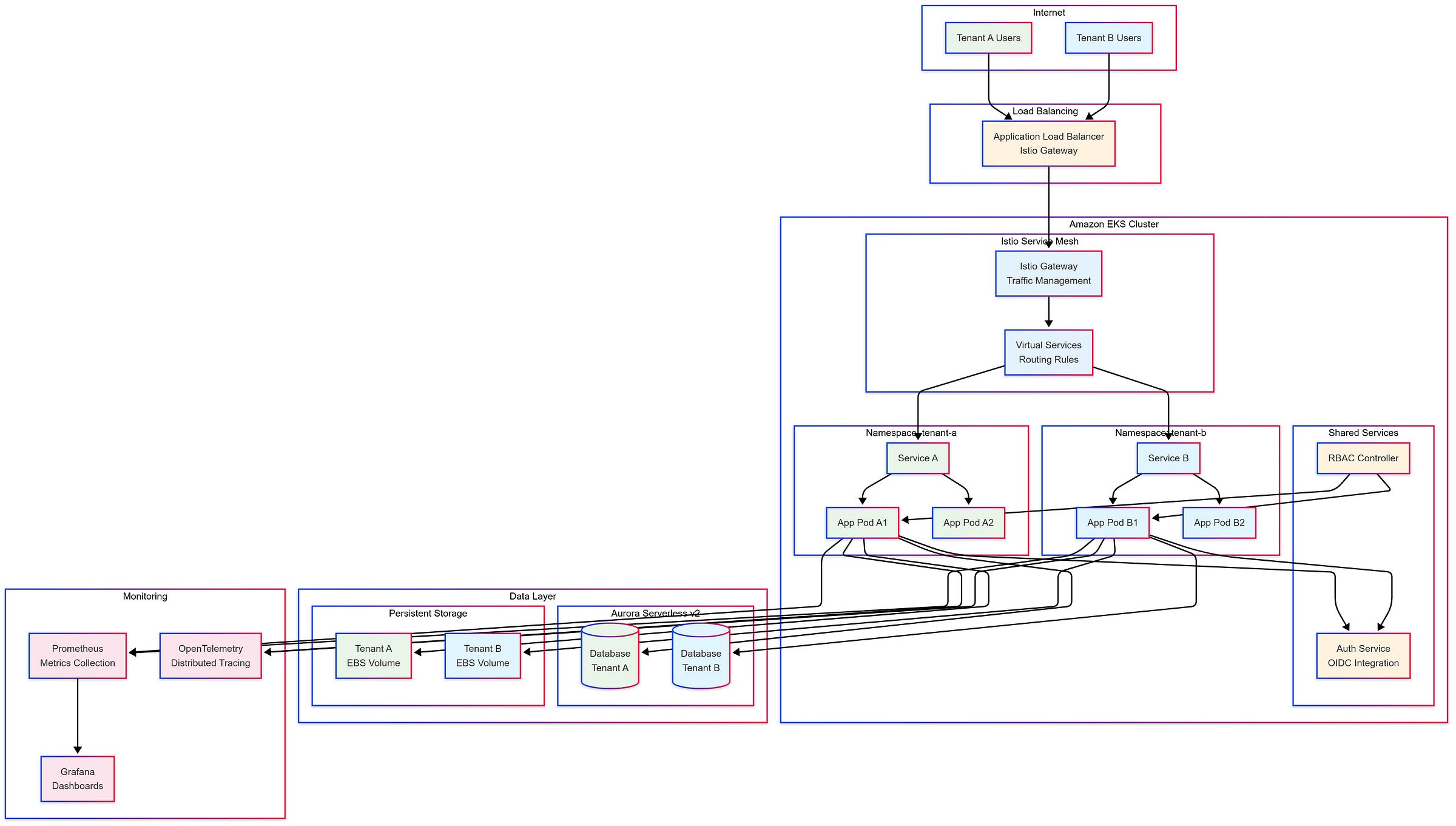
TCP #78: Multitenant Architecture: Kubernetes-First (EKS-based)
Advanced Infrastructure Pattern #4: Why Shared Clusters Are Security Disasters in Disguise
You can also read my newsletters from the Substack mobile app and be notified when a new issue is available.
Become a Founding Member
As a founding member, you will receive:
Everything included in paid subscriber benefits + exclusive toolkits and templates.
High-quality content from my 11+ years of industry experience, where I solve specific business problems in the real world using AWS Cloud. Learn from my actionable insights, strategies, and decision-making process.
Quarterly report on emerging trends, AWS updates, and cloud innovations with strategic insights.
Public recognition in the newsletter under the “Founding Member Spotlight” section.
Early access to deep dives, case studies, and special reports before they’re released to paid subscribers.
This is pattern #4 of the 4-part series of building Multitenant Architectures on AWS.
In case you missed it, here are the links to the previous post.
Pattern #1: TCP #72: The Architect's Guide to Multitenant ECS: Building Scalable Shared Infrastructure
Pattern #2: TCP #74: Multitenant Architecture: Hybrid Tenant Isolation (ECS-based)
Pattern #3: TCP #76: The Serverless-First Multitenancy Revolution
Pattern #4: TCP #78: Multitenant Architecture: Kubernetes-First (EKS-based)
Here's an uncomfortable truth that most Kubernetes experts won't tell you: Your shared EKS cluster is a security disaster waiting to happen.
I know what you're thinking. "But we use labels for tenant separation!" or "Our RBAC is solid!" or "We've never had a security incident."
That's exactly what 89% of the teams I've worked with said, right before a single tenant's misconfiguration brought down their entire platform.
The reality is that shared Kubernetes clusters with tenant labels are a form of technical debt disguised as efficiency.
Every pod, every service, and every secret shares the same security boundary. One privilege escalation, one container breakout, one resource exhaustion attack, and your entire SaaS platform becomes collateral damage.
Meanwhile, a growing number of engineering teams are quietly adopting namespace-per-tenant architectures, which provide true isolation without the operational overhead associated with cluster-per-tenant approaches.
They're achieving enterprise-grade security, simplified troubleshooting, and better resource utilization, all while maintaining the economic benefits of shared infrastructure.
Today, I'll show you why namespace-per-tenant isn't just the future of Kubernetes multitenancy. It's the only approach that scales safely in production environments.