TCP #88: How to Automatically Track End-of-Life Software With Amazon Bedrock Agents (Before It Costs You $20K)
Build autonomous EOL monitoring that catches vulnerabilities hiding in your dependency tree
You can also read my newsletters from the Substack mobile app and be notified when a new issue is available.
Last month, a nested dependency three levels deep in our package tree caused a critical security breach.
It had reached end-of-life six months earlier. Nobody knew it existed. By the time we discovered the vulnerability, active exploits were circulating in the wild.
The recovery: 72 hours of emergency work, external consultants, and $20,000 in direct costs, not counting reputational damage.
Here’s what shocked me: When I audited 10 other production environments, 82% were running EOL software they didn’t know existed.
The average discovery time? Six months after EOL.
The core problem: Modern applications have hundreds of dependencies. Manual tracking is impossible. CVEs explode the moment packages hit EOL, but traditional scanners won’t flag them until it’s too late.
This guide shows you how to build an autonomous system using Amazon Bedrock Agents, which continuously monitor your entire software stack and alert your team with actionable upgrade paths, eliminating the need for manual intervention.
Why Traditional EOL Tracking Fails
Manual spreadsheets become outdated instantly. The moment you document dependencies, new packages get added, and your tracking becomes fiction.
Dependency scanners are reactive. Tools like Dependabot flag CVEs after they’re discovered and documented. When packages hit EOL, there’s often a weeks-long gap before specific vulnerabilities get catalogued.
Nested dependencies are invisible. You might track your 20 direct dependencies, but what about the 200 packages they pull in? A single npm package can have a dependency tree dozens of levels deep.
Cross-ecosystem complexity multiplies. Python microservices, Node.js APIs, Go utilities, and Java batch jobs each have different EOL policies and tracking databases.
Alert fatigue kills effectiveness. Flag every dependency update, and teams learn to ignore the noise. Critical EOL notifications get lost.
This is where AI agents change the game.
How Bedrock Agents Solve This
Amazon Bedrock Agents combine LLMs with action-taking capabilities to create autonomous systems that reason, decide, and execute tasks. Unlike rigid scripts, agents can:
Understand context
When discovering log4j 1.x is EOL, the agent doesn’t just flag it; it explains that log4j 1.x was discontinued in 2015, has critical CVEs, and requires migration to 2.x (not a simple version bump).
Adapt to changing patterns
EOL databases use inconsistent formats. LLM-powered agents parse these variations without custom logic for each source.
Provide human-readable explanations.
Clear descriptions of what’s wrong, why it matters, and what to do, dramatically reducing time from alert to action.
Execute complex workflows autonomously. Check for upgrades, assess compatibility, prioritize by severity, route notifications, all without human intervention.
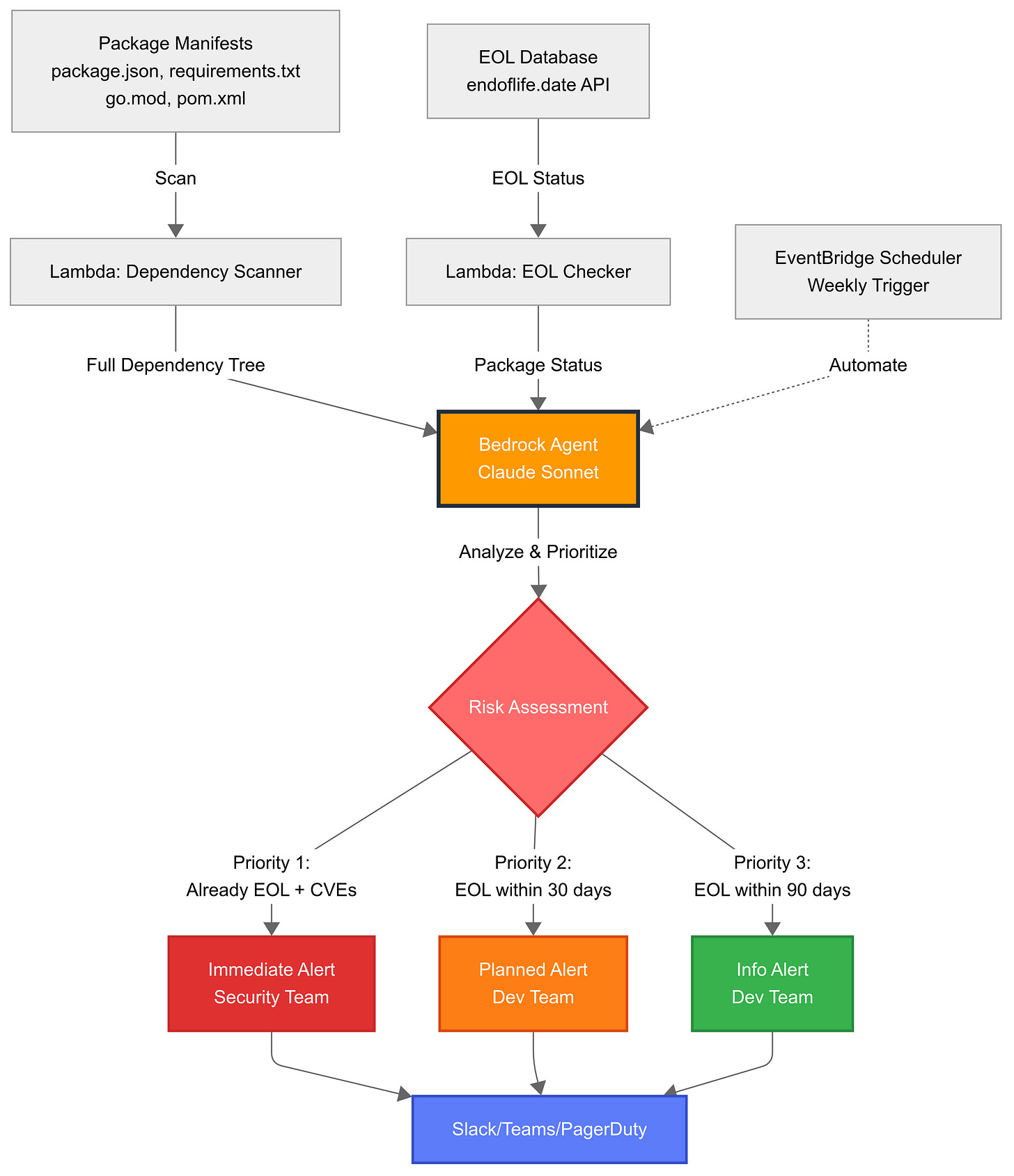
Architecture Overview
Data Layer: Your package manifests (package.json, requirements.txt, go.mod, pom.xml) across all environments—dev, staging, and production.
Knowledge Base: Integration with endoflife.date API, maintaining comprehensive EOL data for hundreds of products.
Action Functions: Lambda functions the agent invokes to scan dependencies, query EOL databases, and retrieve dependency graphs.
Orchestration: Bedrock Agent handles reasoning, decision-making, and workflow coordination.
Alerting: Integration with Slack, Teams, or PagerDuty for routing notifications by severity.
Step-by-Step Implementation
Phase 1: Build Dependency Scanner Functions
Create Lambda functions that read and parse package manifests. You need separate parsers for each package manager:
For Node.js: Parse the package.json and package-lock.json files. The lock file is crucial; it contains exact versions of nested dependencies.
For Python: Parse requirements.txt or Pipfile.lock. Use pip-tree programmatically to generate the full dependency graph.
For Go: Parse go.mod and go.sum. Go’s explicit versioning makes EOL tracking easier.
For Java: Parse pom.xml (Maven) or build.gradle (Gradle). Expect deeply nested trees that require a significant recursion depth.
Critical detail: Scan all environments, not just production. Development and staging are where EOL packages get introduced, and tag results with environment context for prioritization.
Edge case: Monorepos with multiple package managers need separate scan functions for each ecosystem.
Phase 2: EOL Database Integration
Create a Lambda function querying the endoflife.date API. Accept package name and version, return EOL status, support dates, and security notes.
Key optimization: Implement intelligent caching. EOL dates don’t change frequently—cache responses for 24 hours using DynamoDB or ElastiCache.
Performance tip: Batch your API calls. For 100 dependencies, parallelize requests instead of 100 sequential calls. This dramatically reduces Lambda execution time and cost.
Phase 3: Configure Your Bedrock Agent
Create an agent with Claude Sonnet as the foundation model.
Give it clear instructions about monitoring dependencies, identifying EOL packages, and providing upgrade recommendations.
Define action functions with detailed descriptions:
scan_dependencies: “Parses package manifest files from specified repository and environment. Returns complete dependency tree including nested dependencies.”
check_eol_status: “Queries EOL database for specific package and version. Returns EOL date, support status, known vulnerabilities, and recommended upgrade path.”
Prompt engineering matters: Give explicit instructions about priority levels. “Packages already EOL with known CVEs are Priority 1. Packages reaching EOL within 30 days are Priority 2. Within 90 days are Priority 3.”
Phase 4: Implement Intelligent Alerting
Route alerts based on severity and ownership:
Priority 1 (already EOL with security implications): Immediate alerts to the security team and platform owners with specific details, what’s affected, why it matters, and recommended upgrade path.
Priority 2 and 3 (approaching EOL): Informational notifications to development teams with planning time.
Structure your alerts actionably: Don’t say “Package X is EOL.” Say: “Package X reached EOL on [date], has [number] known CVEs including [severity levels], and should be upgraded to version Y. Estimated migration effort: [complexity assessment].”
Phase 5: Automate the Schedule
Use EventBridge to trigger weekly scans, which are frequent enough to catch issues early without constantly processing unchanged data. For critical production, consider daily scans.
Pro optimization: Implement change detection. Before full scans, check if manifests have changed since the last run. If unchanged, skip analysis. This reduces processing and cost dramatically.
Advanced Patterns and Edge Cases
Version ambiguity: npm’s caret (^) and tilde (~) operators, Python’s pip compatibility operators, and Go’s minimum version selection create deployment ambiguity. Always scan lock files for resolved versions.
Private packages: Extend your knowledge base with internal EOL policies. Create a custom database to track the support lifecycles of private packages.
Deprecated vs. EOL: Flag packages in deprecation phase before formal EOL, distinguishing between “maintenance mode,” “deprecated,” and “EOL.”
Cross-dependency conflicts: Sometimes upgrading package A requires upgrading B, C, and breaks D. Your agent can analyze these chains: “To upgrade log4j, first upgrade Spring Framework to version X, which requires Java 11+.”
Runtime EOL: Don’t forget underlying runtimes. Python 3.7, Node.js 12, Java 8 reach EOL too. Track both package-level and runtime-level EOL dates.
Measuring Success
Track these metrics:
Mean time to detection: How quickly does your agent identify new EOL packages? Target completion within 7 days from the EOL date.
False positive rate: Target under 5% through careful prompt engineering.
Coverage percentage: Target 100% across all environments.
Remediation time: Should decrease as teams develop and upgrade workflows.
Common Implementation Mistakes
Scanning only production: Dev and staging are where EOL packages get introduced. Scan everything from the start.
Ignoring nested dependencies: Most critical vulnerabilities hide in transitive dependencies. Traverse the complete dependency graph.
Over-alerting: Use intelligent prioritization. Immediate security risks get loud alerts, and approaching EOL gets informational notifications.
No upgrade paths: Alerting without suggesting compatible versions creates frustration. Let your agent research and recommend.
Skipping lower environment testing: When your agent recommends upgrades, validate them in development and staging environments first.
What’s Next
Once operational, consider these enhancements:
Automatic PRs: Integrate with GitHub/GitLab APIs to automatically create PRs with dependency updates.
Compliance Reporting: Generate reports for security audits that show your EOL package landscape.
Predictive planning: Forecast upcoming EOL dates across your stack for proactive upgrade cycles.
CI/CD integration: Block deployments introducing new EOL dependencies.
Cost optimization: Track deprecated packages with more efficient alternatives.
Final Thoughts
End-of-life software is a silent, growing risk most teams discover only after an incident. Traditional tracking doesn’t scale with the complexity of modern dependencies.
Amazon Bedrock Agents offer an autonomous solution that combines AI reasoning with action-taking capabilities to continuously monitor your software stack—all for less than two lattes per month.
This approach is battle-tested through real-world incidents that have taught us where traditional monitoring falls short. The architecture is production-ready, costs are negligible, and potential cost avoidance from prevented incidents is substantial.
Whenever you’re ready, there are 3 ways I can help you:
Want to build automated, AI-powered businesses without quitting your job? Join my free community: The AI Business Playbook
Free guides and helpful resources: https://thecloudplaybook.gumroad.com/
Get certified as an AWS AI Practitioner in 2025. Sign up today to elevate your cloud skills. (link)
That’s it for today!
Did you enjoy this newsletter issue?
Share with your friends, colleagues, and your favorite social media platform.
Until next week — Amrut
Get in touch
You can find me on LinkedIn or X.
If you would like to request a topic to read, please feel free to contact me directly via LinkedIn or X.