TCP #71: The Multi-Tenant Security Breach That Changed Everything
A deep dive into API Gateway Custom Authorizers for tenant-aware security
You can also read my newsletters from the Substack mobile app and be notified when a new issue is available.
Become a Founding Member
As a founding member, you will receive:
Everything included in paid subscriber benefits + exclusive toolkits and templates.
High-quality content from my 11+ years of industry experience, where I solve specific business problems in the real world using AWS Cloud. Learn from my actionable insights, strategies, and decision-making process.
Quarterly report on emerging trends, AWS updates, and cloud innovations with strategic insights.
Public recognition in the newsletter under the “Founding Member Spotlight” section.
Early access to deep dives, case studies, and special reports before they’re released to paid subscribers.
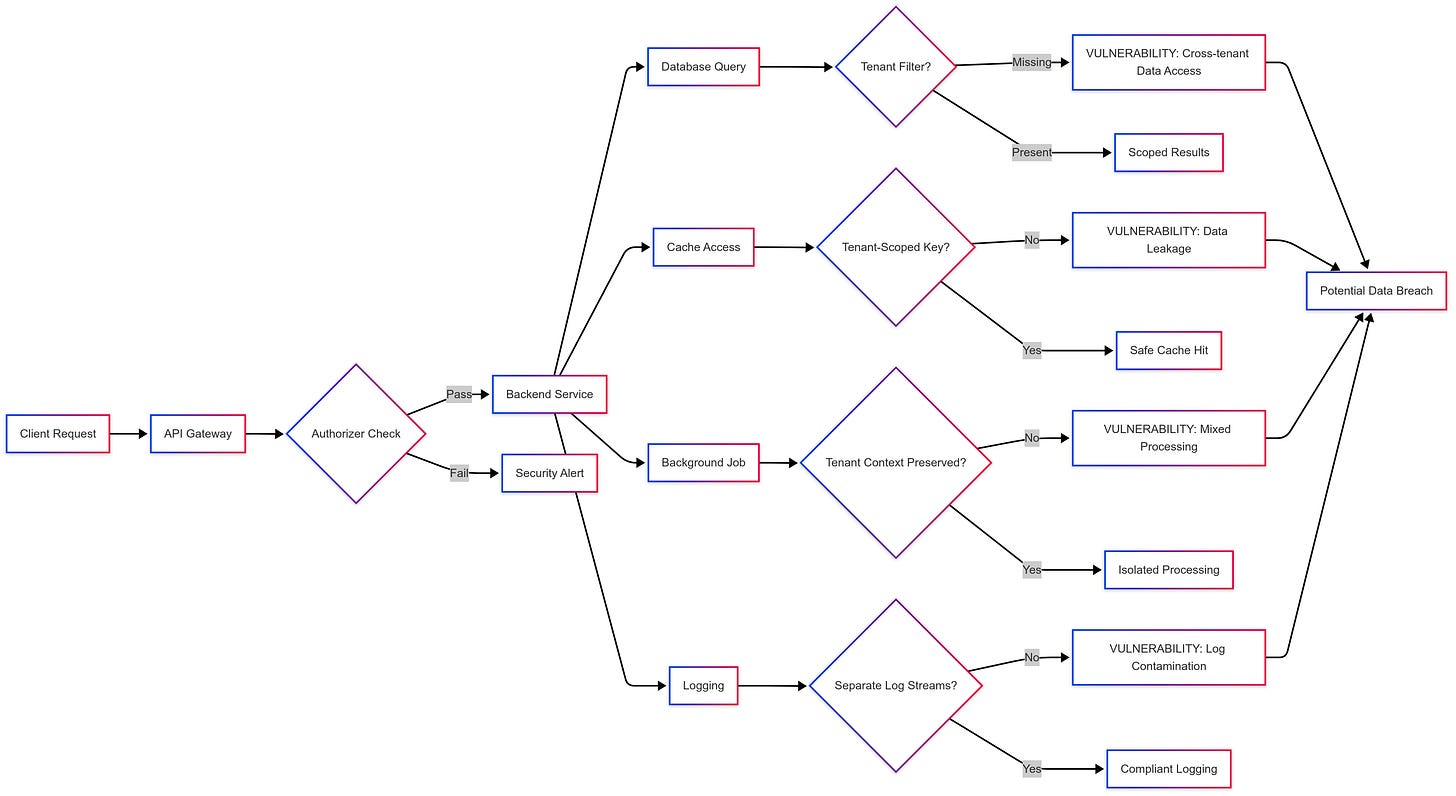
Last month, while reviewing our AWS CloudTrail logs, I noticed something that made my stomach drop.
A user from Tenant A had successfully retrieved customer records belonging to Tenant B. Our "secure" multi-tenant SaaS platform had a fundamental flaw that could have compromised our entire system.
The fix was deceptively simple, one line of code in our API Gateway authorizer.
But the journey to understand why it happened and how to prevent it everywhere revealed a pattern that most developers get catastrophically wrong.
This isn't about JWT validation or basic authentication. This is about the invisible security boundary that separates your customers' most sensitive data.
Beyond "Who Are You?": The Tenant Context Problem
Traditional API security focuses on identity verification:
Is this token valid? Does this user exist?
But multi-tenant applications operate in a different reality. They need to answer three critical questions in sequence:
1. Authentication: Who is making this request?
2. Tenant Resolution: Which tenant context does this user belong to?
3. Authorization: What can this user access within their tenant boundary?
Most developers nail the first question and completely botch the second two.
The result? Cross-tenant data leakage that can destroy customer trust overnight.
The challenge isn't technical complexity. It's recognizing that tenant context must be treated as a first-class security primitive, not an afterthought.
The Hidden Failure Points
Your application probably has tenant context bleeding in places you haven't considered:
Database queries that don't scope to tenant boundaries
Cache keys that accidentally share data between tenants
Background jobs that process data without tenant awareness
Logging systems that mix tenant data in the same log streams
Each represents a potential compliance violation and a breach of customer trust.
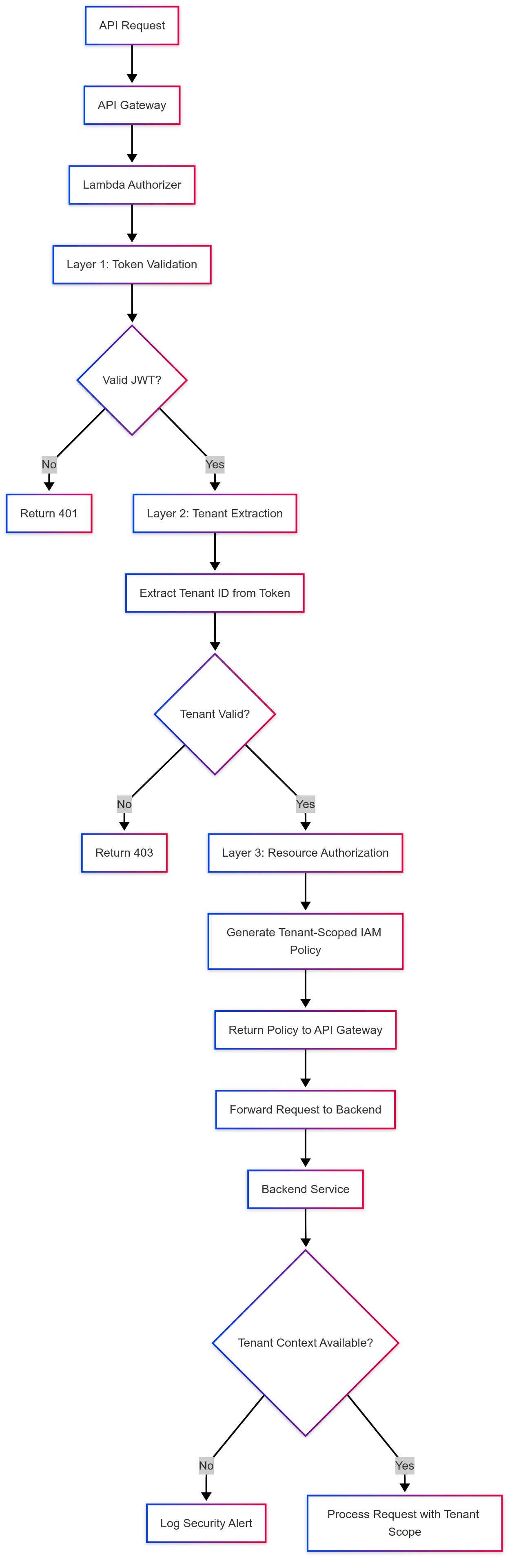
The Three-Layer Authorization Architecture
Effective tenant-aware authorization requires a structured approach.
Here's the pattern that's served us reliably across multiple production environments:
Layer 1: Token Validation
Standard JWT verification, but with tenant-specific considerations. Your tokens should carry tenant claims that can't be manipulated client-side. This means signing tokens with tenant-specific secrets or including tenant hashes in the signature validation.
Layer 2: Tenant Context Extraction
This is where most implementations fail. You need to reliably extract tenant context from multiple potential sources: JWT claims, request headers, URL paths, or even subdomain parsing. The key is establishing a clear hierarchy of tenant resolution and failing securely when context is ambiguous.
Layer 3: Resource Authorization
The final layer ensures users can only access resources within their tenant boundary. This isn't just about database filtering. It extends to file storage, cache access, and even the allocation of compute resources.
Implementation Strategy
Your Lambda authorizer becomes the enforcement point for all three layers.
The critical insight is that the tenant context must be established early and passed through every subsequent service call. Here's the pattern:
// Extract tenant context from multiple sources
const tenantId = extractTenantContext(event)
// Validate user belongs to this tenant
validateUserTenant(userId, tenantId)
// Generate tenant-scoped permissions
return generateTenantScopedPolicy(tenantId, userPermissions)
The authorization response should include the tenant context that downstream services can trust without re-validation.
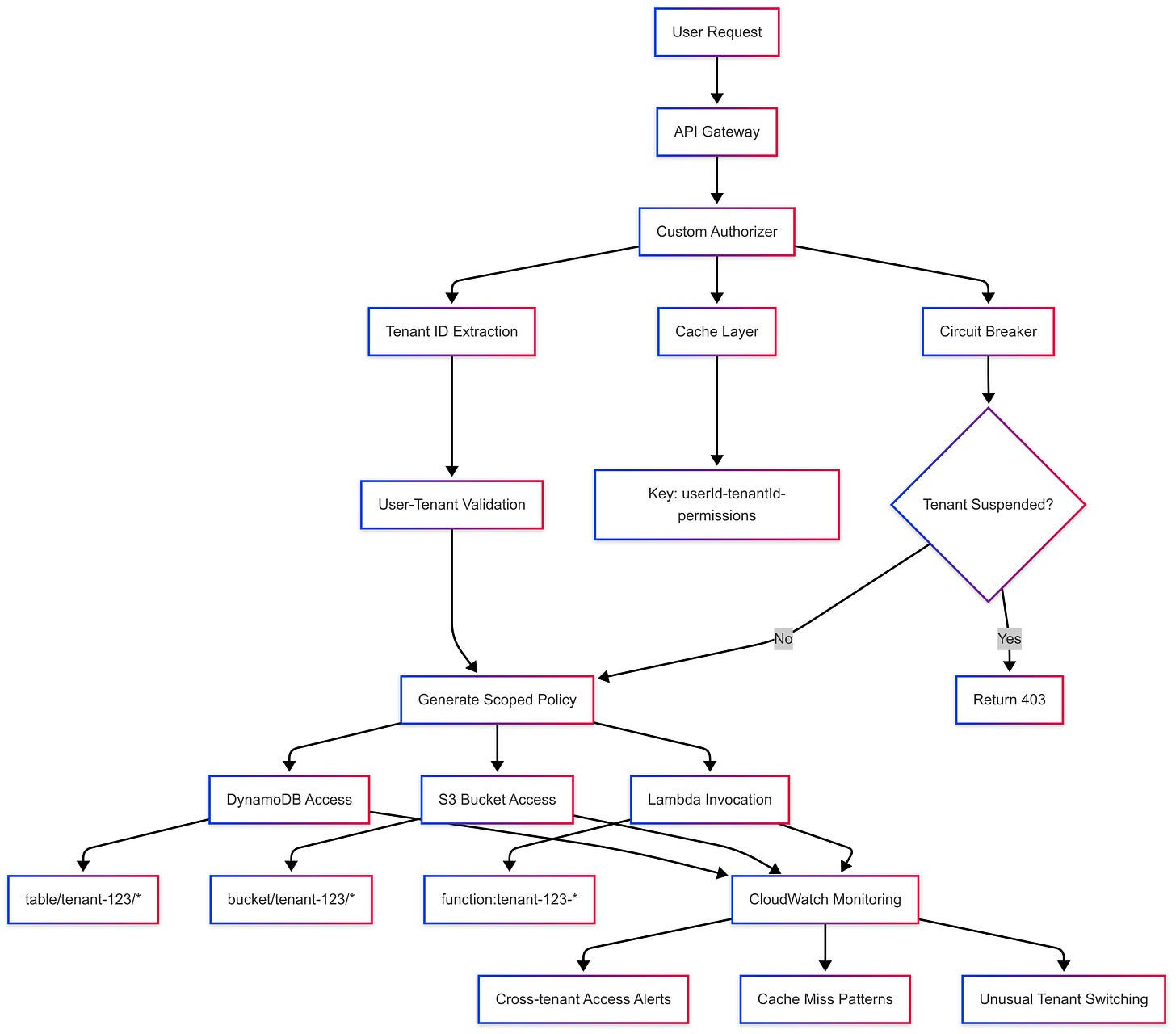
Advanced Tenant Scoping Techniques
Dynamic IAM Policy Generation
Instead of static permissions, generate IAM policies that embed tenant boundaries directly. This approach leverages AWS's native authorization engine to enforce tenant isolation at the infrastructure level.
Your policies should include tenant-specific resource ARNs that make cross-tenant access impossible:
DynamoDB table partitions are scoped to the tenant
S3 bucket prefixes that enforce tenant boundaries
Lambda function permissions that can only invoke tenant-specific resources
Attribute-Based Access Control
Role-based permissions don't scale in complex multi-tenant environments. Implement attribute-based access control that evaluates multiple factors:
User attributes: Role, department, security clearance level
Resource attributes: Data classification, creation date, owner
Environmental attributes: Time of access, IP location, device type
Tenant attributes: Subscription level, compliance requirements, geographical restrictions
This granular approach prevents privilege escalation attacks and provides fine-grained audit trails.
Tenant Hierarchy Support
Many SaaS applications need to support organizational hierarchies, including parent companies with subsidiary access, reseller relationships, or departmental structures. Your authorizer needs to understand these relationships and grant appropriate cross-tenant permissions while maintaining security boundaries.
Performance Optimization Without Security Compromise
Intelligent Caching Strategies
Authorizer caching can dramatically improve API performance, but it introduces security risks if implemented incorrectly. The cache key must include all security-relevant context:
${userId}-${tenantId}-${permissionSet}-${requestType}
Never cache authorizer responses that could be reused across tenant boundaries. A single cache collision can leak sensitive data to unauthorized tenants.
Connection Pooling and Database Optimization
Tenant-aware applications frequently struggle with managing database connections. Consider implementing tenant-specific connection pools to prevent query contamination and improve performance isolation. Your database queries should always include tenant filters as the first WHERE clause condition.
Edge Case Handling
Performance optimization reveals edge cases that can become security vulnerabilities:
Cache warming scenarios where background processes access multiple tenants
Cross-tenant reporting requirements that need carefully controlled data aggregation
Tenant migration processes that temporarily require elevated permissions
Emergency access patterns for customer support or incident response
Each scenario needs specific authorization logic that maintains security while enabling necessary functionality.
Real-World Troubleshooting and Incident Response
Detecting Cross-Tenant Access Attempts
Implement monitoring that treats any cross-tenant access attempt as a potential security incident.
Your CloudWatch metrics should track:
Authorization failures by tenant and user
Unusual tenant switching patterns
Resource access outside normal user patterns
Cache miss rates that could indicate attack attempts
Set up automated alerts for anomalies. They often indicate either misconfigured applications or active attacks.
The Circuit Breaker Pattern
When a security incident occurs, you need the ability to instantly isolate affected tenants without disrupting your entire service. Implement a circuit breaker in your authorizer that can:
Immediately suspend access for specific tenants
Enable read-only mode during investigations
Log all access attempts for forensic analysis
Provide graceful degradation rather than complete service failure
Incident Containment Procedures
Your incident response should include tenant-specific containment procedures:
Immediate isolation: Block all access to the affected tenant data
Forensic preservation: Capture logs and access patterns before they rotate
Impact assessment: Determine what data was accessed and by whom
Customer communication: Notify affected tenants with specific details
Remediation verification: Ensure fixes prevent similar future incidents
Testing Strategies That Actually Work
Security-First Test Design
Your integration tests must validate failure modes, not just success paths. Critical test scenarios include:
Tenant boundary violations: Valid users attempting to access the wrong tenant data
Token manipulation: Modified JWT claims attempting to escalate tenant access
Race conditions: Concurrent requests during tenant context switches
Cache poisoning: Attempts to contaminate authorization caches
Replay attacks: Using valid tokens outside their intended tenant context
Automated Security Scanning
Implement automated tests that continuously validate tenant isolation:
Database queries that accidentally omit tenant filters
API endpoints that don't properly validate the tenant context
Cache implementations that could leak data between tenants
Background processes that don't maintain tenant boundaries
Load Testing with Tenant Awareness
Performance testing should simulate realistic multi-tenant load patterns. This reveals security issues that only appear under stress:
Authorization cache failures during high load
Database connection pool exhaustion affecting tenant isolation
Memory pressure causing cross-tenant data corruption
Rate limiting failures that could enable denial-of-service attacks
Advanced Implementation Patterns
Multi-Region Tenant Distribution
Global SaaS applications often distribute tenants across regions for compliance or performance reasons. Your authorization layer needs to understand tenant geography and ensure users can only access data in appropriate regions.
Tenant Data Classification
Implement data classification schemes that work with your authorization layer. Different data types within the same tenant may require different access controls, such as financial data versus usage analytics.
Compliance Integration
Modern authorization systems must integrate with compliance frameworks. Your tenant-aware authorizer should support:
GDPR requirements: Data minimization and purpose limitation
SOC 2 controls: Access logging and approval workflows
HIPAA compliance: Minimum necessary access principles
Industry regulations: Sector-specific data handling requirements
Emergency Access Procedures
Despite perfect authorization controls, you'll occasionally need emergency access to tenant data. Implement break-glass procedures that:
Require multiple approvals for emergency access
Log all emergency access with business justification
Automatically expire emergency permissions
Notify affected tenants when appropriate
The Path Forward
Multi-tenant security isn't a destination. It's an ongoing practice that evolves with your application and threat landscape.
The authorization patterns I’ve covered form a foundation, but your specific implementation will need customization based on your tenant model, compliance requirements, and risk tolerance.
The key insight is treating tenant context as a security boundary that's as important as user authentication. Every service call, database query, and cache access should carry tenant context and validate it appropriately.
Next Steps
Audit your current implementation: Where does the tenant context get lost or ignored?
Implement comprehensive logging: You can't secure what you can't see
Test your failure modes: Security vulnerabilities live in edge cases
Plan your incident response: How quickly can you isolate a compromised tenant?
Educate your team: Multi-tenant security requires organization-wide awareness.
Final Thoughts
Tenant context is a first-class security primitive that must be validated at every system boundary.
Authorization caching requires careful implementation to prevent cross-tenant data leakag.e
Performance optimization and security aren't mutually exclusive when designed thoughtfull.y
Incident response capabilities are critical for maintaining customer trust
Testing must focus on security failure modes rather than just functional requirements
The $50K breach we prevented was ultimately caused by treating tenant context as an application concern rather than a security boundary. Don't make the same mistake.
SPONSOR US
The Cloud Playbook is now offering sponsorship slots in each issue. If you want to feature your product or service in my newsletter, explore my sponsor page
That’s it for today!
Did you enjoy this newsletter issue?
Share with your friends, colleagues, and your favorite social media platform.
Until next week — Amrut
Get in touch
You can find me on LinkedIn or X.
If you wish to request a topic you would like to read, you can contact me directly via LinkedIn or X.