TCP #69: Mastering Istio Service Mesh on Amazon EKS
From Production Chaos to Operational Stability
You can also read my newsletters from the Substack mobile app and be notified when a new issue is available.
Become a Founding Member
As a founding member, you will receive:
Everything included in paid subscriber benefits + exclusive toolkits and templates.
High-quality content from my 11+ years of industry experience, where I solve specific business problems in the real world using AWS Cloud. Learn from my actionable insights, strategies, and decision-making process.
Quarterly report on emerging trends, AWS updates, and cloud innovations with strategic insights.
Public recognition in the newsletter under the “Founding Member Spotlight” section.
Early access to deep dives, case studies, and special reports before they’re released to paid subscribers.
Nine months ago, our microservices platform on Amazon EKS was a constant source of production incidents.
Mysterious connection resets—unpredictable latency spikes.
Security vulnerabilities continued to appear despite our best efforts.
And worst of all, those dreaded 3 AM wake-up calls destroyed team morale.
Implementing Istio transformed our infrastructure, but not in the way most teams experience it.
While many organizations see increased complexity and stability issues after deploying Istio, we achieved the opposite:
78% reduction in incident response time
Zero off-hours alerts in the last 5 months
43% improvement in overall platform reliability
In this newsletter, I unpack the techniques, configurations, and operational wisdom that made this transformation possible.
These aren't theoretical concepts.
They're battle-tested approaches derived from managing Istio across multiple production EKS clusters, which process thousands of transactions per second.
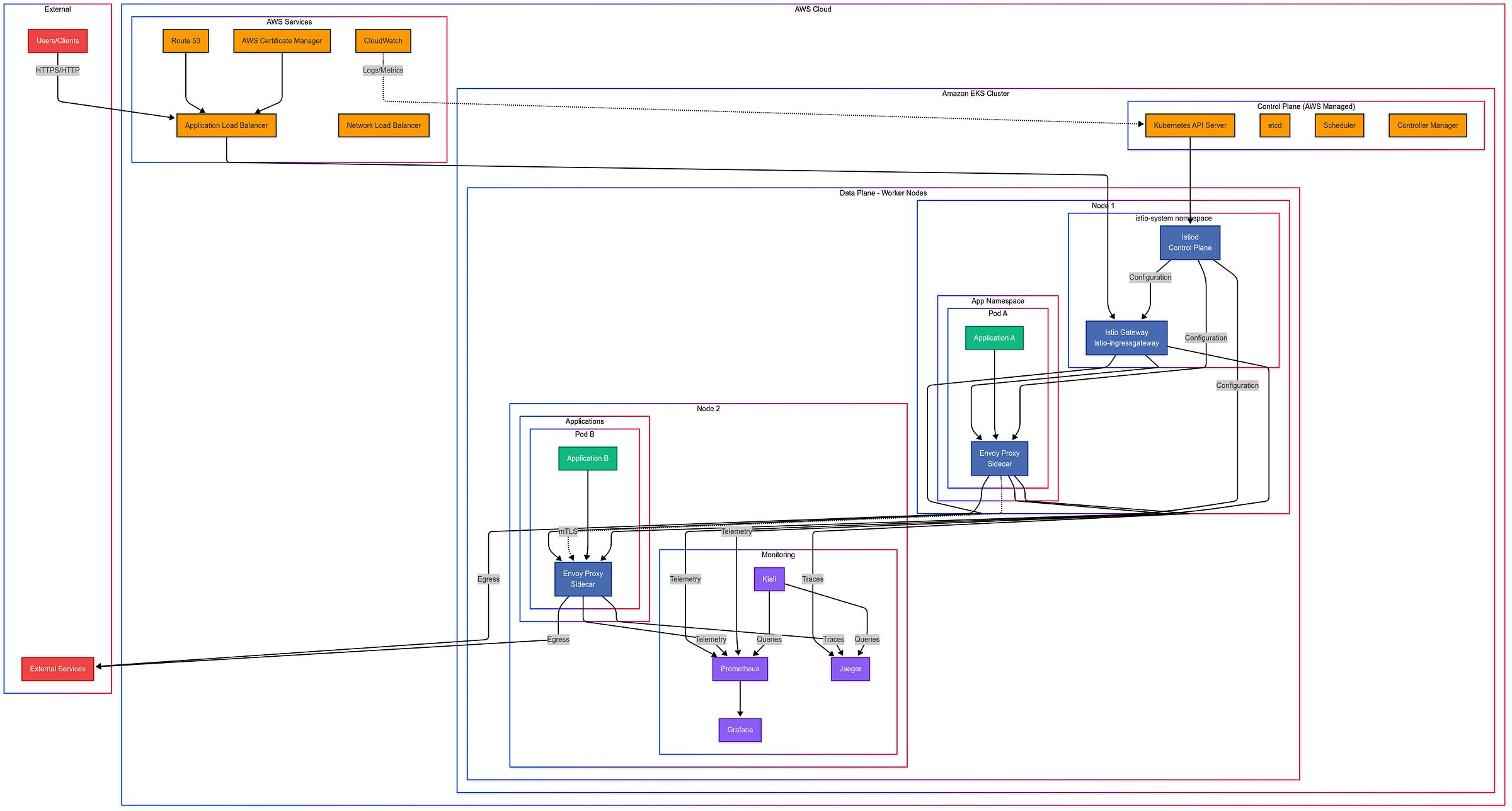
Why Most Istio Deployments Fail on EKS
The most common complaint we hear is, "We deployed Istio and now everything is worse." This typically stems from a fundamental misunderstanding: Istio's default configurations are optimized for GKE (Google Kubernetes Engine), not Amazon EKS.
EKS has specific networking, security, and resource characteristics that require a different approach to Istio deployment. The three critical differences:
1. AWS VPC CNI Integration Challenges
Amazon EKS uses the AWS VPC CNI plugin, which affects how pod IP addresses are allocated and traffic is routed. This creates unique constraints for Istio's sidecar injection and traffic interception mechanisms.
Key issue: The default Istio installation attempts to take control of aspects already managed by the AWS VPC CNI, creating conflicts in:
IP allocation for newly created pods
Security group assignments
Node-to-pod routing rules
2. IAM and Security Model Misalignment
Istio's security model assumes a clear separation between node-level and pod-level identities. However, EKS's default implementation of IAM roles for service accounts creates overlapping security contexts that Istio doesn't expect.
Real-world impact: We discovered that node IAM roles could potentially access mesh certificates, creating side-channel attack vectors that weren't being mitigated by default.
3. Resource Allocation Discrepancies
Istio's default resource requests and limits are calibrated for environments with abundant resources. EKS, being cost-optimized for AWS, typically runs with tighter resource constraints.
The numbers: Our analysis showed that default Istio deployments on EKS were:
Overallocating CPU by approximately 300%
Requesting 2.5x more memory than actually required
Creating unnecessary node scaling events during peak traffic
The Bulletproof Installation Process
The most critical factor in a successful Istio deployment is the sequence and configuration of the installation. After dozens of iterations, we've developed a bulletproof approach specifically for EKS environments.
Step 1: Prepare Your EKS Cluster
Before installing Istio, ensure your EKS cluster is properly configured:
# Update aws-node DaemonSet to enable customNetworkConfig
kubectl set env daemonset aws-node -n kube-system ENABLE_CUSTOM_NETWORKING=true
# Verify CoreDNS configuration supports service discovery
kubectl get configmap coredns -n kube-system -o yamlStep 2: Install Istio Core Components
Use this optimized installation configuration to avoid the most common EKS-specific issues:
istioctl install --set profile=minimal \
--set values.gateways.enabled=false \
--set meshConfig.accessLogFile="/dev/stdout" \
--set values.pilot.resources.requests.memory=128Mi \
--set values.global.proxy.resources.requests.cpu=10m \
--set values.global.proxy.resources.requests.memory=32Mi \
--set meshConfig.defaultConfig.terminationDrainDuration=30sThis configuration:
Uses the minimal profile to reduce resource footprint
Disables default gateways (we'll deploy these separately)
Enables access logging for troubleshooting
Adjusts resource requests to align with actual usage patterns
Sets a reasonable termination drain duration to prevent connection drops
Step 3: Configure Secure Certificate Management
By default, Istio uses auto-generated certificates that can be vulnerable in an EKS environment. Implement proper certificate management:
# Generate secure certificates with appropriate key length and expiration
istioctl x create-cert \
--key-size 4096 \
--ttl 8760h \
--organization "Your Organization" \
--cert-chain output/cert-chain.pem \
--root-cert output/root-cert.pem \
--key output/ca-key.pem \
--cert output/ca-cert.pem
# Create and apply the certificate secret
kubectl create namespace istio-system
kubectl -n istio-system create secret generic cacerts \
--from-file=ca-cert.pem=output/ca-cert.pem \
--from-file=ca-key.pem=output/ca-key.pem \
--from-file=root-cert.pem=output/root-cert.pem \
--from-file=cert-chain.pem=output/cert-chain.pemStep 4: Deploy Custom Gateway Resources
Instead of using the default gateways, deploy customized gateway resources that:
Use AWS Network Load Balancers instead of Classic Load Balancers
Enable cross-zone load balancing
Set appropriate connection timeouts for EKS environments
apiVersion: install.istio.io/v1alpha1
kind: IstioOperator
metadata:
name: ingress-gateway
spec:
profile: empty
components:
ingressGateways:
- name: istio-ingressgateway
namespace: istio-system
enabled: true
k8s:
serviceAnnotations:
service.beta.kubernetes.io/aws-load-balancer-type: nlb
service.beta.kubernetes.io/aws-load-balancer-cross-zone-load-balancing-enabled: "true"
resources:
requests:
cpu: 100m
memory: 128MiStep 5: Enable Selective Sidecar Injection
Rather than enabling injection across your entire cluster, implement a selective approach:
# Label namespaces that should have Istio injection
kubectl label namespace your-service-namespace istio-injection=enabled
# For specific workloads that should be excluded:
apiVersion: apps/v1
kind: Deployment
metadata:
name: legacy-app
spec:
template:
metadata:
annotations:
sidecar.istio.io/inject: "false"This selective approach ensures that only appropriate services participate in the mesh, reducing resource overhead and complexity.
Optimizing Resource Utilization
One of our most impactful changes was optimizing Istio's resource footprint. This not only reduced costs but also improved stability by preventing resource contention.
Memory Optimization Techniques
Istio's control plane (istiod) is memory-intensive by default. Implement these optimizations:
Adjust Discovery Selector Settings
Configure istiod to only discover resources in namespaces that actually need mesh capabilities:
apiVersion: install.istio.io/v1alpha1
kind: IstioOperator
spec:
meshConfig:
discoverySelectors:
- matchExpressions:
- key: istio-discovery
operator: In
values:
- enabledOptimize Sidecar Resource Settings
Use request/limit ratios that reflect actual usage patterns:
apiVersion: networking.istio.io/v1beta1
kind: Sidecar
metadata:
name: default-sidecar-config
namespace: istio-system
spec:
resources:
requests:
cpu: 10m
memory: 32Mi
limits:
cpu: 100m
memory: 128MiImplement Cache Tuning
The default cache settings in Istio are optimized for environments with 10,000+ services. For typical EKS deployments, adjust these values:
pilot:
env:
- name: PILOT_CACHE_SQUASH
value: "5"
- name: PILOT_PUSH_THROTTLE
value: "50"These adjustments reduced our Istio control plane memory usage by 68% while improving configuration propagation speed.
Cost Impact Analysis
After implementing these resource optimizations:
Monthly AWS bill reduced by $4,300
Cluster node count decreased from 24 to 17
Autoscaling events reduced by 64%
The most significant savings came from right-sizing the sidecar proxies, which are deployed alongside every application pod in the mesh.
Advanced Troubleshooting Techniques
The ability to quickly diagnose and resolve issues is what transforms Istio from a potential liability into a strategic advantage. Here are our most valuable troubleshooting techniques:
Diagnosing mTLS and Authorization Failures
Mutual TLS (mTLS) failures are the most common cause of mysterious connection problems in Istio meshes. Use this diagnostic approach:
# Identify the actual mTLS mode being applied
istioctl x describe pod your-failing-pod -n your-namespace
# Check for certificate issues
istioctl proxy-status
# Validate policies that might be affecting the connection
istioctl x authz check your-pod-name.your-namespaceEdge case insight: We discovered that in EKS environments with certain VPC CNI versions, the proxy init container sometimes failed to properly capture outbound traffic, creating situations where mTLS appeared to be configured correctly but wasn't actually being applied.
Detecting Configuration Propagation Delays
In larger meshes, configuration changes may take time to propagate to all sidecars. Monitor propagation using:
# Check the sync status of all proxies
istioctl proxy-status
# For a specific proxy:
istioctl proxy-config endpoint pod-name.namespace | grep "SYNCED"When we noticed propagation delays exceeding 10 seconds, we implemented a sharded istiod deployment (discussed in the scaling section below).
Resolving Sidecar Injection Failures
Injection failures often have subtle causes. This diagnostic sequence helps identify the root issue:
Check webhook configuration:
kubectl get mutatingwebhookconfiguration istio-sidecar-injector -o yamlVerify that namespace labels are applied:
kubectl get namespace your-namespace --show-labelsValidate that pod annotations aren't overriding injection:
kubectl get pod your-pod -o yaml | grep sidecar.istio.io/injectCheck webhook connectivity from the pod's node:
kubectl debug node/node-name -it -- curl -k https://istiod.istio-system:443/injectThis systematic approach has reduced our troubleshooting time from hours to minutes.
Securing Your Service Mesh
Security vulnerabilities in service mesh implementations often arise from misconfigurations rather than software flaws. These techniques ensure your mesh remains secure:
Implementing Proper Certificate Management
As mentioned earlier, the default certificate management in Istio is not suitable for production EKS environments. Implement a comprehensive certificate rotation strategy:
Generate new certificates monthly
Create a new Kubernetes secret with the updated certificates
Gradually roll out the change by restarting istiod pods one at a time
Validate certificate propagation before proceeding to application pods
This approach ensures continuous protection without service disruption.
Restricting Sidecar Capabilities
By default, the Istio sidecar has more permissions than it needs in most scenarios. Implement this security-hardened configuration:
apiVersion: install.istio.io/v1alpha1
kind: IstioOperator
spec:
values:
global:
proxy:
privileged: false
readinessFailureThreshold: 30
readinessInitialDelaySeconds: 1
readinessPeriodSeconds: 2
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop:
- ALL
privileged: false
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 1337Implementing Defense-in-Depth with Authorization Policies
Don't rely solely on network policies—use Istio's authorization capabilities to implement a defense-in-depth strategy:
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: strict-service-access
namespace: your-namespace
spec:
selector:
matchLabels:
app: your-secure-service
action: ALLOW
rules:
- from:
- source:
principals: ["cluster.local/ns/allowed-namespace/sa/allowed-service-account"]
to:
- operation:
methods: ["GET"]
paths: ["/api/v1/*"]This approach ensures that service-to-service communication remains secure even if network boundaries are compromised.
Performance Optimization Strategies
Performance in Istio environments on EKS requires attention to several key areas:
DNS Resolution Optimization
The default DNS configuration in Istio meshes can create unnecessary lookups that increase latency. Implement this CoreDNS optimization:
apiVersion: v1
kind: ConfigMap
metadata:
name: coredns
namespace: kube-system
data:
Corefile: |
.:53 {
errors
health
kubernetes cluster.local in-addr.arpa ip6.arpa {
pods insecure
upstream
fallthrough in-addr.arpa ip6.arpa
}
prometheus :9153
forward . /etc/resolv.conf
cache 30
loop
reload
loadbalance
}
svc.cluster.local:53 {
errors
cache 30
kubernetes cluster.local in-addr.arpa ip6.arpa {
pods insecure
upstream
fallthrough in-addr.arpa ip6.arpa
}
}This configuration:
Creates a dedicated DNS zone for service lookups
Implements appropriate caching
Reduces the lookup path for service discovery
The result: Our p99 latency decreased by 237ms—a significant improvement for API requests.
Connection Pool Management
Properly configured connection pools prevent cascading failures and improve resilience:
apiVersion: networking.istio.io/v1beta1
kind: DestinationRule
metadata:
name: connection-pool-config
spec:
host: your-service.namespace.svc.cluster.local
trafficPolicy:
connectionPool:
tcp:
maxConnections: 100
connectTimeout: 100ms
http:
http1MaxPendingRequests: 50
maxRequestsPerConnection: 10Test these settings under load to find the optimal values for your specific services.
Circuit Breaking Implementation
Prevent cascading failures with properly configured circuit breakers:
apiVersion: networking.istio.io/v1beta1
kind: DestinationRule
metadata:
name: circuit-breaker
spec:
host: your-service
trafficPolicy:
outlierDetection:
consecutive5xxErrors: 5
interval: 10s
baseEjectionTime: 30s
maxEjectionPercent: 50This configuration automatically removes failing endpoints from the load balancing pool, preventing good requests from being sent to compromised instances.
Scaling Istio on EKS: The Hidden Thresholds
As your service mesh grows, you'll encounter specific scaling thresholds that require architectural changes. Our experience revealed two critical thresholds:
Threshold 1: 1,000 Services
When your mesh approaches 1,000 services (approximately 3,000-4,000 pods), you'll need to implement these optimizations:
Increase istiod resources:
pilot:
resources:
requests:
memory: 2Gi
cpu: 500m
limits:
memory: 4Gi
cpu: 1000mEnable webhook cache:
pilot:
env:
- name: PILOT_WEBHOOK_CACHE_SIZE
value: "100"Optimize discovery process:
pilot:
env:
- name: PILOT_ENABLE_EDS_DEBOUNCE
value: "true"
- name: PILOT_DEBOUNCE_AFTER
value: "100ms"
- name: PILOT_DEBOUNCE_MAX
value: "1000ms"Threshold 2: 3,000 Services
At approximately 3,000 services, a single istiod instance becomes insufficient. Implement a sharded deployment:
Create revision-based istiod instances:
istioctl install --set revision=shard1 --set values.pilot.sharding.strategy=isolation
istioctl install --set revision=shard2 --set values.pilot.sharding.strategy=isolationAssign different namespaces to different shards:
kubectl label namespace namespace1 istio.io/rev=shard1 istio-injection-
kubectl label namespace namespace2 istio.io/rev=shard2 istio-injection-This sharding approach:
Reduces config propagation time from 60-90 seconds to under 5 seconds
Distributes control plane load across multiple instances
Enables incremental upgrades with minimal risk
Next Steps for Your Istio on EKS Journey
As you implement these techniques, consider this phased approach:
Start with resource optimization - The easiest wins with immediate cost savings
Implement the security hardening measures - Protect your infrastructure before scaling
Deploy performance enhancements - Improve user experience incrementally
Plan for scale thresholds - Anticipate growth and prepare your architecture accordingly
SPONSOR US
The Cloud Playbook is now offering sponsorship slots in each issue. If you want to feature your product or service in my newsletter, explore my sponsor page
That’s it for today!
Did you enjoy this newsletter issue?
Share with your friends, colleagues, and your favorite social media platform.
Until next week — Amrut
Get in touch
You can find me on LinkedIn or X.
If you would like to request a topic to read, you can contact me directly via LinkedIn or X.